Aup Policy Template
Aup Policy Template - This acceptable usage policy covers the security and use of all (acme corporation’s) information and it equipment. Unsure of how to develop your school’s acceptable use policy (aup)? Key elements of an effective rup. The acceptable use policy (aup) process is a methodical framework designed to establish guidelines for responsible and secure use of an organisation’s technology resources. The aup helps your company’s cyber security. Sans has developed a set of information security policy templates. An acceptable use policy template serves as the scaffolding for building a tailored set of guidelines specific to the nature and needs of the. The purpose of this policy is to outline the acceptable use of computer equipment at [agency name]. This template encompasses a broad spectrum of. Our list includes policy templates. These are free to use and fully customizable to your company's it security practices. We have developed a comprehensive and customizable acceptable use policy (aup) template for it administrators. Download our free acceptable usage policy (aup) template and learn how to protect your business from it risks. Create your own acceptable use policy with our free acceptable use policy template. This acceptable usage policy covers the security and use of all (acme corporation’s) information and it equipment. Key elements of an effective rup. Institutional neutrality is neither a necessary condition for academic freedom nor categorically incompatible with it. Essential guide for 2025 cybersecurity. It also includes the use of email, internet, voice and mobile it What is an acceptable use policy template? This acceptable usage policy covers the security and use of all (acme corporation’s) information and it equipment. These are free to use and fully customizable to your company's it security practices. This policy highlights the unique issues raised by genai, helps employees understand the guidelines for its acceptable use, and protects the company’s confidential or sensitive. Our list includes policy. Here, we list some prime examples of aup documents, related permissions slips, and aup checklists. The purpose of this acceptable use policy (the “policy”) is to outline acceptable use of technology at the company and to ensure the risks associated with inappropriate or unauthorized use of. Essential guide for 2025 cybersecurity. This template encompasses a broad spectrum of. The acceptable. An acceptable use policy template serves as the scaffolding for building a tailored set of guidelines specific to the nature and needs of the. It also includes the use of email, internet, voice and mobile it Download our free acceptable usage policy (aup) template and learn how to protect your business from it risks. The aup helps your company’s cyber. Here, we list some prime examples of aup documents, related permissions slips, and aup checklists. Key elements of an effective rup. It also includes the use of email, internet, voice and mobile it The statement calls for principles of academic freedom and. The purpose of this acceptable use policy (the “policy”) is to outline acceptable use of technology at the. Essential guide for 2025 cybersecurity. We have developed a comprehensive and customizable acceptable use policy (aup) template for it administrators. This policy highlights the unique issues raised by genai, helps employees understand the guidelines for its acceptable use, and protects the company’s confidential or sensitive. This acceptable usage policy covers the security and use of all (acme corporation’s) information and. Essential guide for 2025 cybersecurity. These rules are in place to protect the employee and [agency name]. The purpose of this acceptable use policy (the “policy”) is to outline acceptable use of technology at the company and to ensure the risks associated with inappropriate or unauthorized use of. Unsure of how to develop your school’s acceptable use policy (aup)? The. These rules are in place to protect the employee and [agency name]. Download our free acceptable usage policy (aup) template and learn how to protect your business from it risks. The acceptable use policy (aup) process is a methodical framework designed to establish guidelines for responsible and secure use of an organisation’s technology resources. The aup helps your company’s cyber. Unsure of how to develop your school’s acceptable use policy (aup)? The purpose of this acceptable use policy (the “policy”) is to outline acceptable use of technology at the company and to ensure the risks associated with inappropriate or unauthorized use of. The purpose of this policy is to outline the acceptable use of computer equipment at [agency name]. Key. The purpose of this policy is to outline the acceptable use of computer equipment at [agency name]. The acceptable use policy (aup) process is a methodical framework designed to establish guidelines for responsible and secure use of an organisation’s technology resources. This policy highlights the unique issues raised by genai, helps employees understand the guidelines for its acceptable use, and. This template encompasses a broad spectrum of. An acceptable use policy (aup) is a document where you let users know what is acceptable and what is not acceptable when using your service or platform, as well as what. The purpose of this policy is to outline the acceptable use of computer equipment at [agency name]. The purpose of this acceptable. The purpose of this acceptable use policy (the “policy”) is to outline acceptable use of technology at the company and to ensure the risks associated with inappropriate or unauthorized use of. It also includes the use of email, internet, voice and mobile it These rules are in place to protect the employee and [agency name]. Create your own acceptable use policy with our free acceptable use policy template. What is an acceptable use policy template? Essential guide for 2025 cybersecurity. An acceptable use policy template serves as the scaffolding for building a tailored set of guidelines specific to the nature and needs of the. Download our free acceptable usage policy (aup) template and learn how to protect your business from it risks. This policy highlights the unique issues raised by genai, helps employees understand the guidelines for its acceptable use, and protects the company’s confidential or sensitive. Institutional neutrality is neither a necessary condition for academic freedom nor categorically incompatible with it. The purpose of this policy is to outline the acceptable use of computer equipment at [agency name]. Here, we list some prime examples of aup documents, related permissions slips, and aup checklists. Our list includes policy templates. We have developed a comprehensive and customizable acceptable use policy (aup) template for it administrators. The acceptable use policy (aup) process is a methodical framework designed to establish guidelines for responsible and secure use of an organisation’s technology resources. Sans has developed a set of information security policy templates.Acceptable Use Policy Acceptable Use Policy Template
Acceptable Use Policy 20182025 Form Fill Out and Sign Printable PDF
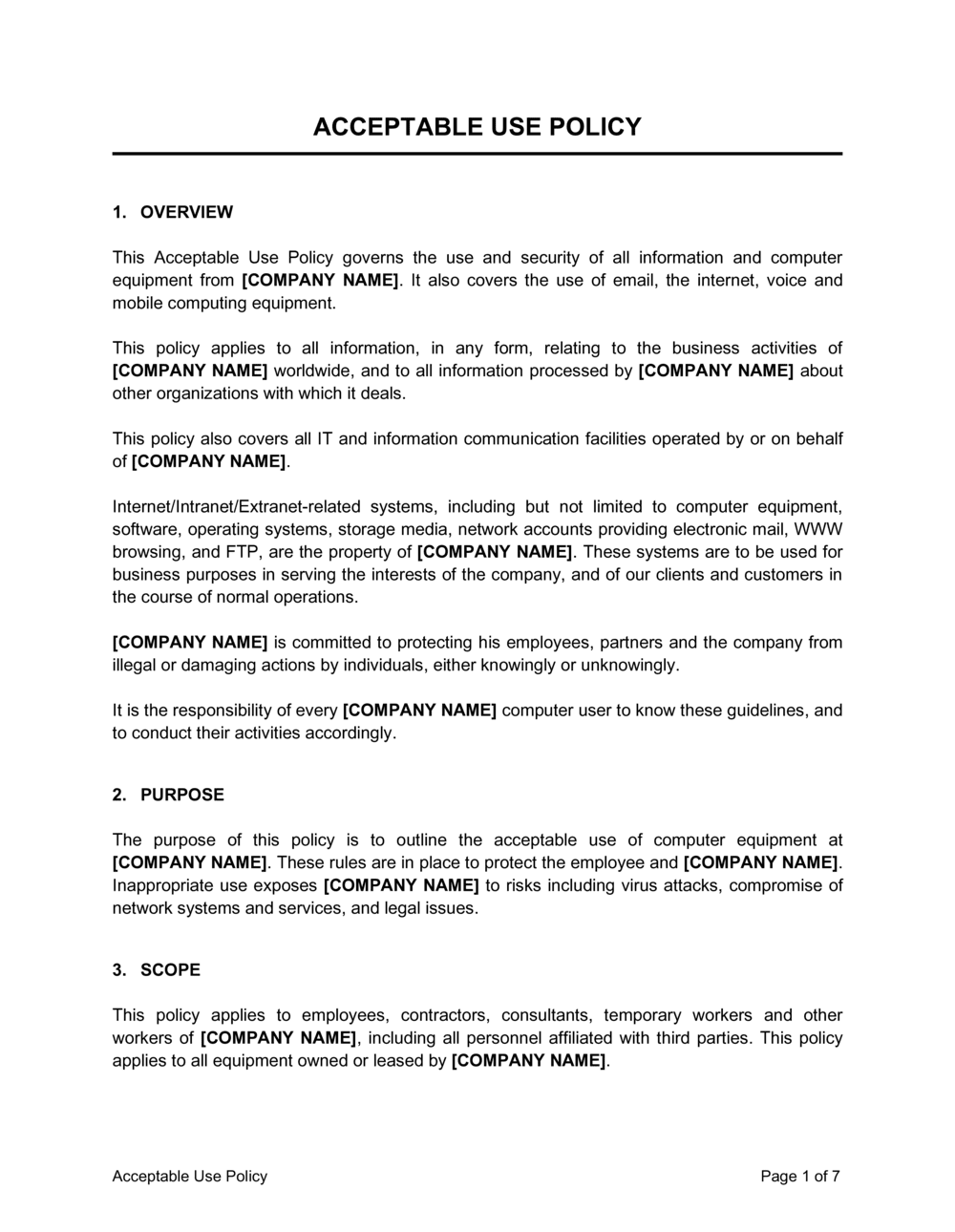
Acceptable Use Policy Template Word
Employee Acceptable Use Policy Template
Acceptable Use Policy Template 2 Free Templates in PDF, Word, Excel
Aup Policy Template
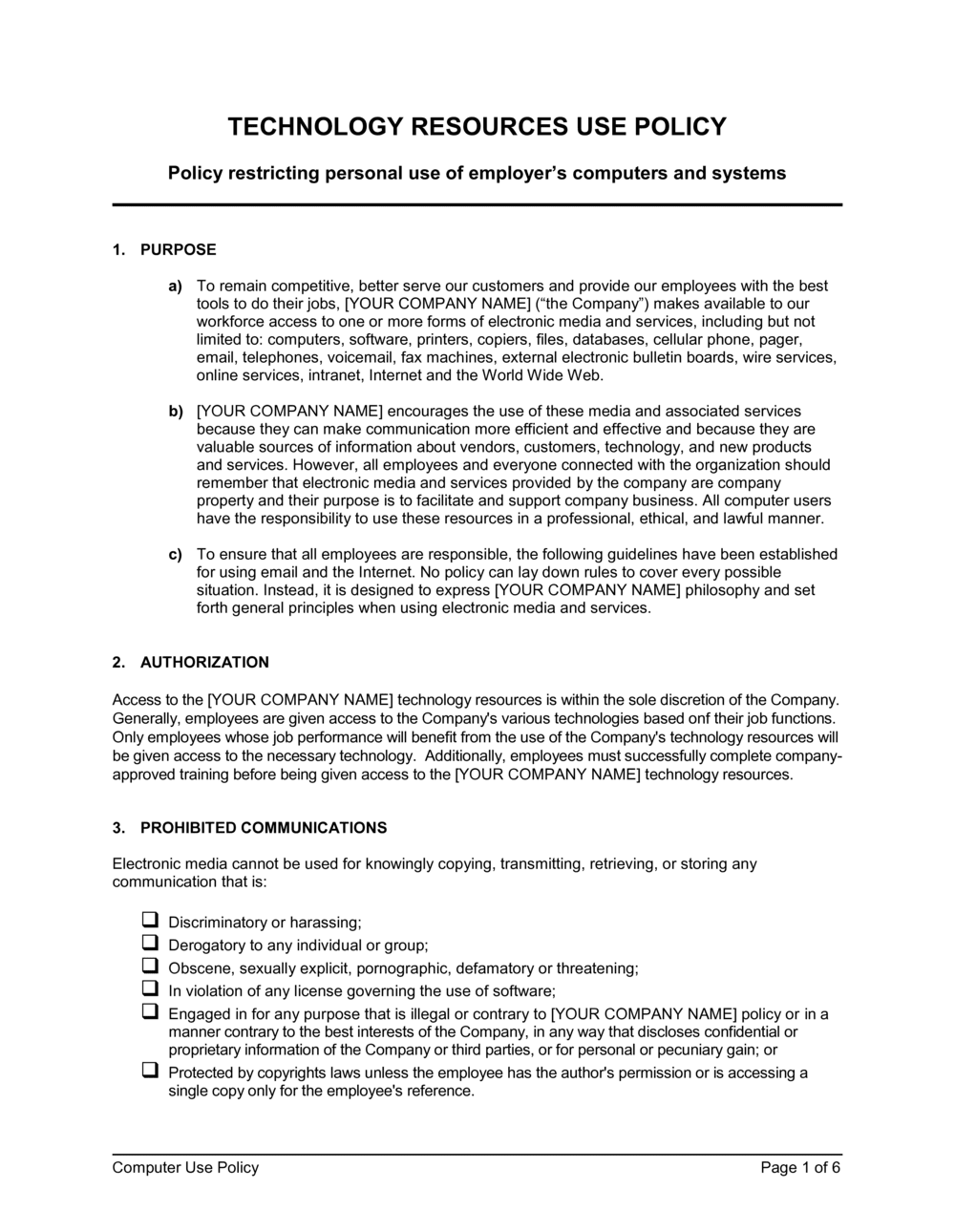
Employee Computer Use Policy Template
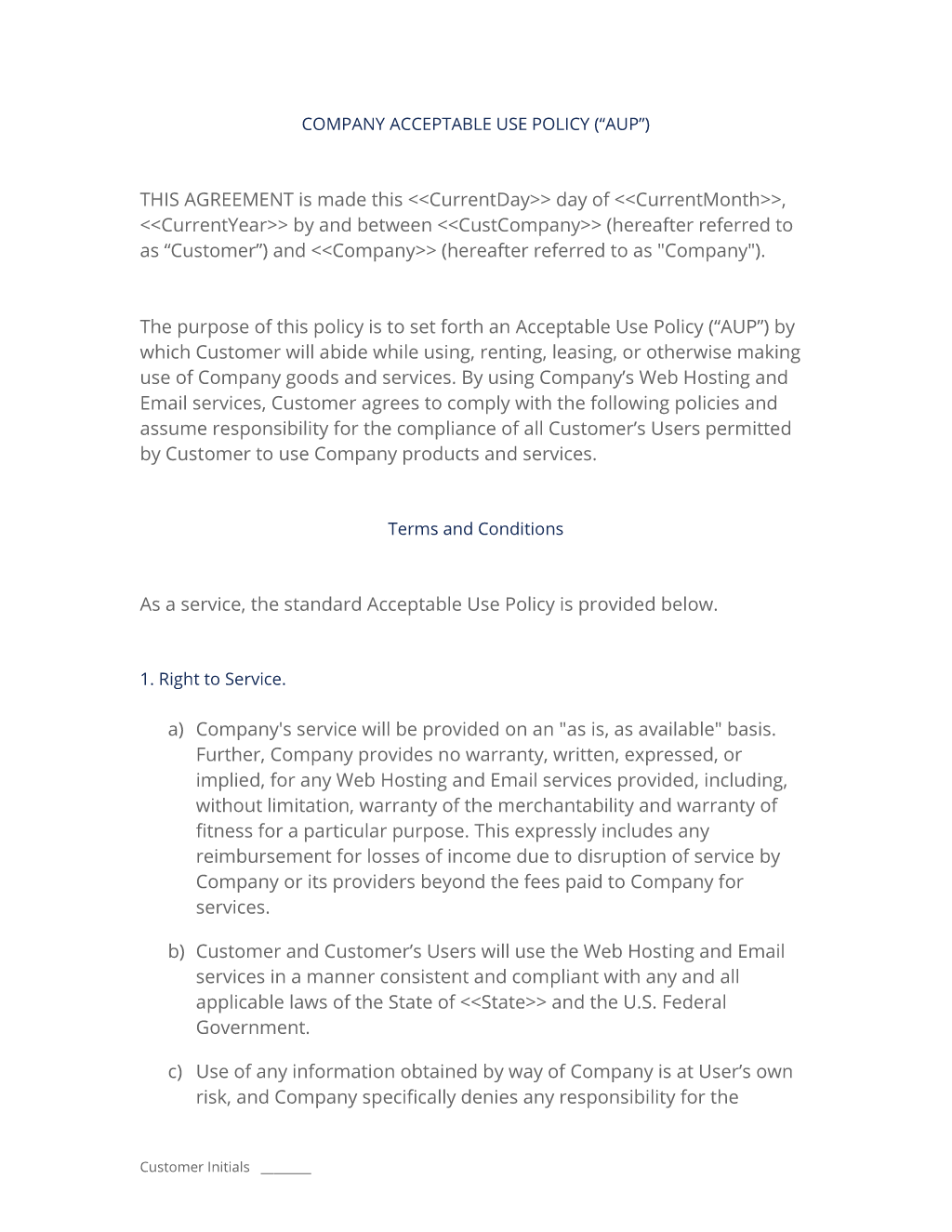
Acceptable Use Policy Template by BusinessinaBox™
Acceptable Use Policy Template 2 Free Templates in PDF, Word, Excel
Acceptable Use Policy Template 3 Easy Steps
The Aup Helps Your Company’s Cyber Security.
These Are Free To Use And Fully Customizable To Your Company's It Security Practices.
The Statement Calls For Principles Of Academic Freedom And.
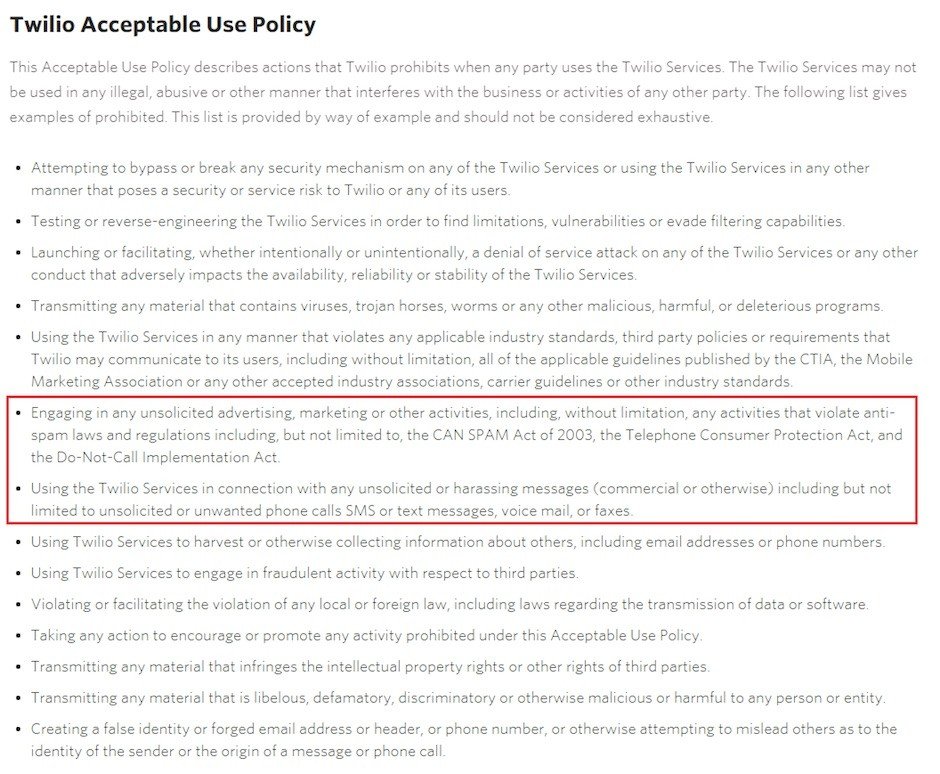
This Acceptable Usage Policy Covers The Security And Use Of All (Acme Corporation’s) Information And It Equipment.
Related Post: