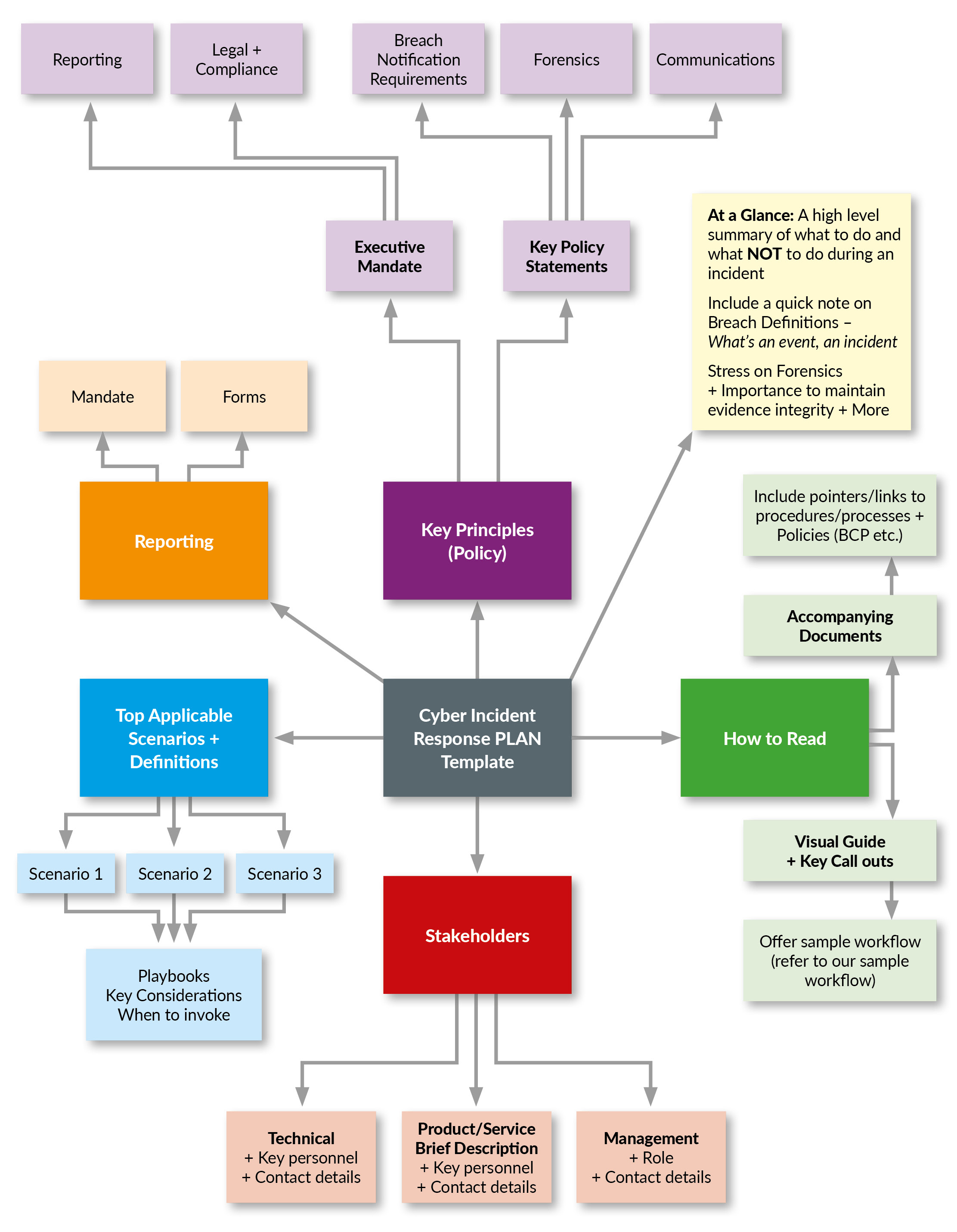
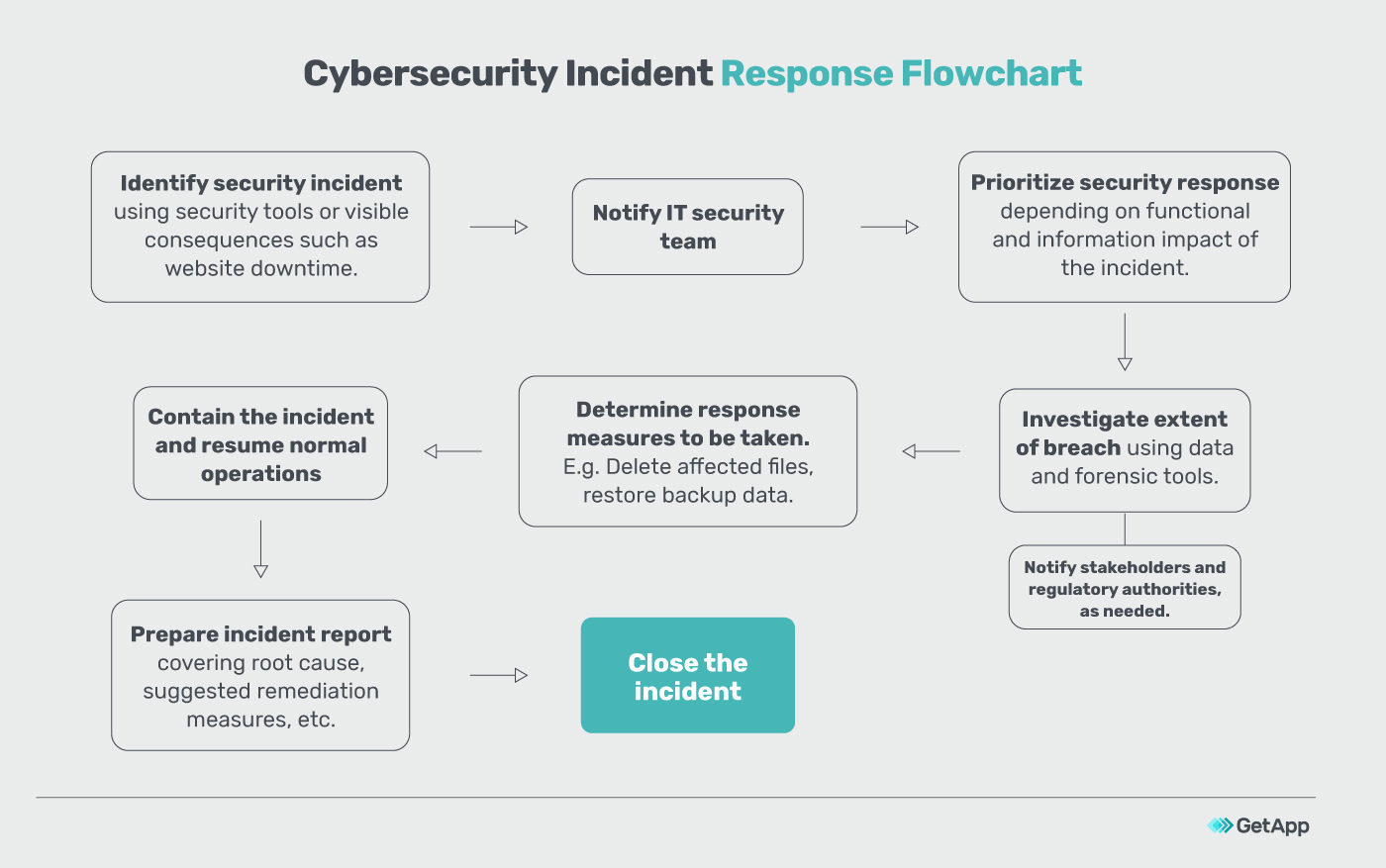
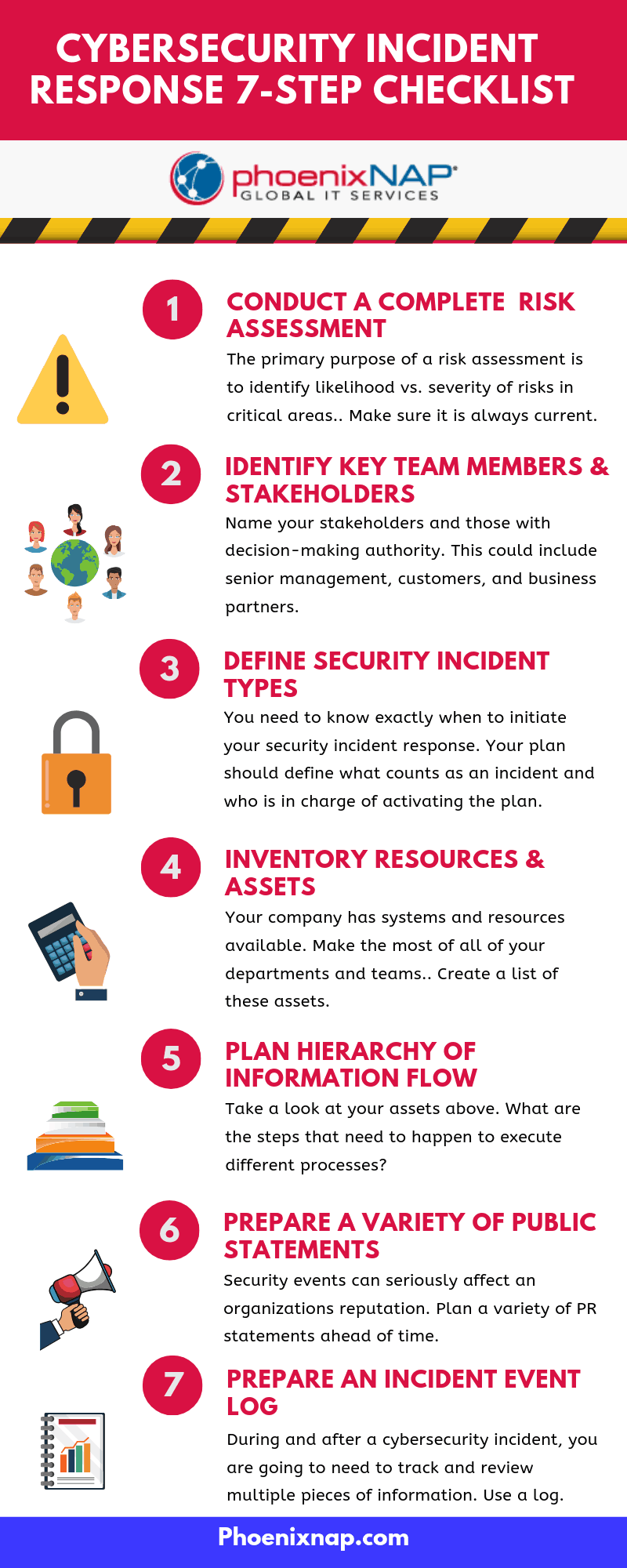
Cyber Incident Response Plan Template
Cyber Incident Response Plan Template - These stages form a systematic approach to handling. 5 steps to building an incident response plan. Create your own concise, flexible, and free incident response plan here, based on our compilation of best practices. An it contingency plan template is an indispensable tool for organizations seeking to protect their technological infrastructure against unforeseen disruptions. There are several resources that can help you develop your incident response plan. The response should limit the potential. This template was developed by the team at counteractive security, to help all organizations get a good start on a concise, directive, specific, flexible, and free incident response plan. Cyberspace effects implementation and operation protection and. The guide provides direction on how a cyber security incident response plan should be formulated and what steps a disaster recovery plan should contain. In today’s digital world, cyber threats are on the rise. The more mature and sophisticated the irp becomes, the more. These playbooks provide fceb agencies with a standard set of procedures to identify, coordinate, remediate, recover, and track successful mitigations from incidents and. A strong cybersecurity incident response plan is essential to detect, respond to, and mitigate security breaches efficiently. An comprehensive plan to help businesses prepare for a cyber incident. Cyberspace effects implementation and operation protection and. The response should limit the potential. Let us know who you are? Acknowledging that breaches are inevitable, organizations must prepare for rapid incident detection, containment and recovery. This template was developed by the team at counteractive security, to help all organizations get a good start on a concise, directive, specific, flexible, and free incident response plan. These stages form a systematic approach to handling. Eticulously finetune the processes for their company. The response should limit the potential. When a cyber security incident occurs, timely and thorough action to manage the impact of the incident is a critical to an effective response process. What is an incident response. 5 steps to building an incident response plan. Focus on preparedness and incident response. Execute key portions of a cyber incident response plan after its development; An it contingency plan template is an indispensable tool for organizations seeking to protect their technological infrastructure against unforeseen disruptions. Let us know who you are? Techtarget's free, editable incident response plan template can help organizations develop a customized approach to help. An it contingency plan template is an indispensable tool for organizations seeking to protect their technological infrastructure against unforeseen disruptions. The response should limit the potential. The more mature and sophisticated the irp becomes, the more. An incident response (ir) plan is a documented approach to address and manage cybersecurity incidents or attacks. A strong cybersecurity incident response plan is. The response should limit the potential. The guide provides direction on how a cyber security incident response plan should be formulated and what steps a disaster recovery plan should contain. In addition to nist, there is sans incident. Execute key portions of a cyber incident response plan after its development; Acknowledging that breaches are inevitable, organizations must prepare for rapid. These stages form a systematic approach to handling. The response should limit the potential. Cyberspace effects implementation and operation protection and. In addition to nist, there is sans incident. Eticulously finetune the processes for their company. How to build an incident response plan around the 6 phases of incident response, examples to get you started, and a peek at incident response automation. The guide provides direction on how a cyber security incident response plan should be formulated and what steps a disaster recovery plan should contain. These playbooks provide fceb agencies with a standard set of. An comprehensive plan to help businesses prepare for a cyber incident. When a cyber security incident occurs, timely and thorough action to manage the impact of the incident is a critical to an effective response process. These stages form a systematic approach to handling. Simply input your information and press enter to see the. A strong cybersecurity incident response plan. An incident response plan (irp) is a structured and documented set of procedures designed to guide an organization’s response to. 5 steps to building an incident response plan. Techtarget's free, editable incident response plan template can help organizations develop a customized approach to help them detect and respond to security incidents. These stages form a systematic approach to handling. Cyberspace. What is an incident response. An incident response (ir) plan is a documented approach to address and manage cybersecurity incidents or attacks. How to build an incident response plan around the 6 phases of incident response, examples to get you started, and a peek at incident response automation. 5 steps to building an incident response plan. To create such a. An it contingency plan template is an indispensable tool for organizations seeking to protect their technological infrastructure against unforeseen disruptions. What is an incident response. This template was developed by the team at counteractive security, to help all organizations get a good start on a concise, directive, specific, flexible, and free incident response plan. There are several resources that can. Ns prepare for and respond to incidents of all sizes. Focus on preparedness and incident response. Execute key portions of a cyber incident response plan after its development; Acknowledging that breaches are inevitable, organizations must prepare for rapid incident detection, containment and recovery. What is an incident response plan? These stages form a systematic approach to handling. The more mature and sophisticated the irp becomes, the more. The guide provides direction on how a cyber security incident response plan should be formulated and what steps a disaster recovery plan should contain. Simply input your information and press enter to see the. An it contingency plan template is an indispensable tool for organizations seeking to protect their technological infrastructure against unforeseen disruptions. Download our incident response plan template today! How to build an incident response plan around the 6 phases of incident response, examples to get you started, and a peek at incident response automation. An comprehensive plan to help businesses prepare for a cyber incident. Let us know who you are? When a cyber security incident occurs, timely and thorough action to manage the impact of the incident is a critical to an effective response process. The response should limit the potential.Incident cyber response template plan structure planning immediately
Cyber Security Incident Response Plan Template Printable Word Searches
Incident Response Plan Cyber Security Template
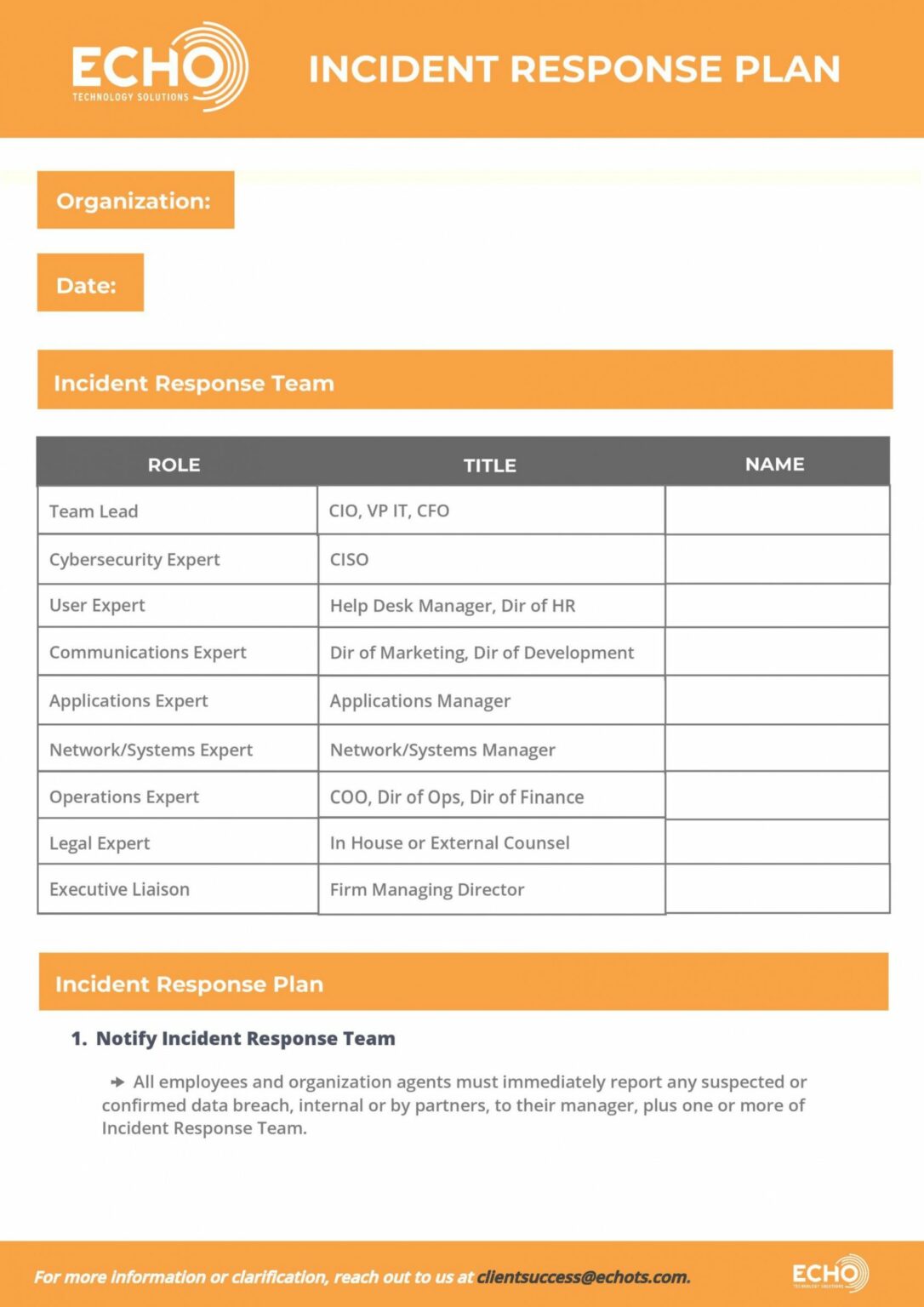
Incident Response Plan Template
Cyber Security Response Plan Template
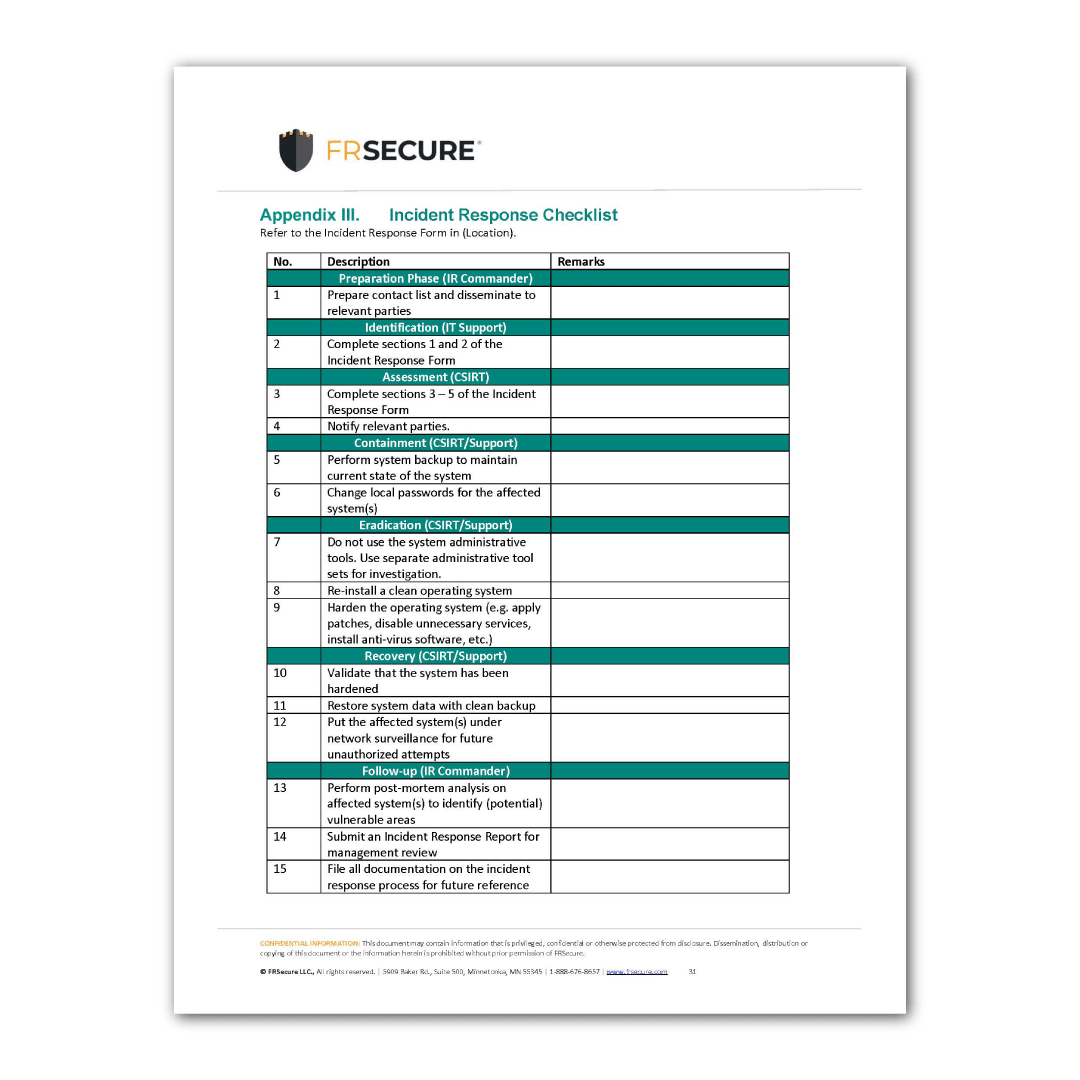
Cyber Incident Response Form Template in Word, PDF, Google Docs
Incident Response Plan Template
Cyber Incident Response Plan Template
Cyber Security Incident Response Plan Template
Incident Response Plan Template
Techtarget's Free, Editable Incident Response Plan Template Can Help Organizations Develop A Customized Approach To Help Them Detect And Respond To Security Incidents.
5 Steps To Building An Incident Response Plan.
An Incident Response (Ir) Plan Is A Documented Approach To Address And Manage Cybersecurity Incidents Or Attacks.
Cyberspace Effects Implementation And Operation Protection And.
Related Post: