Cyber Security Report Template
Cyber Security Report Template - They enable you to compile comprehensive reports that. Download and edit a professional cyber security report example. Our free printable templates help you log risks, incidents, controls and recommendations. Cyber security under the reporting standards. Simplify documentation of breaches, viruses, and other it security events. Neglecting strong, thoroughly tested, and dependable security measures can leave you vulnerable to malicious attacks. Download in xls & pdf formats. Writing an effective cybersecurity incident report is a critical step in incident response. Six months after the sec’s cybersecurity incident disclosure rule (sec rule) came into force, an april 2024 gt alert summarized disclosure trends. What is an incident response report? Create the perfect defence against cyber crimes with our comprehensive security report templates. If cybersecurity is identified as a material topic and falls. They enable you to compile comprehensive reports that. Some 72% of respondents report an increase in organizational cyber risks, with ransomware remaining a top concern. Here we present to you our top 5 security report templates to explain the need and importance of a security report. Get insights and templates to enhance your cybersecurity documentation How is this report done? Security safeguards to ensure cyber resilience. Cyber security under the reporting standards. Browse upguard's library of free templates for all major cybersecurity standards, frameworks and regulations. Six months after the sec’s cybersecurity incident disclosure rule (sec rule) came into force, an april 2024 gt alert summarized disclosure trends. How to write a cybersecurity incident report. These templates offer a streamlined, professional solution to the complex challenges of cyber security reporting. Using a structured cyber incident report template, firms efficiently communicate details related to a security breach. Using a structured cyber incident report template, firms efficiently communicate details related to a security breach or incident. Simplify documentation of breaches, viruses, and other it security events. In this article, you’ll find the most effective cybersecurity risk assessment templates for project managers, security analysts, security incident responders, intrusion detection. Here we present to you our top 5 security report. Simplify documentation of breaches, viruses, and other it security events. Download and edit a professional cyber security report example. Security safeguards to ensure cyber resilience. The cyber risk assessment powerpoint template is a visually structured tool designed to help businesses, it teams, and security professionals analyze and present cyber threats. In this article, you’ll find the most effective cybersecurity risk. Safeguard your business with a robust security report. Writing an effective cybersecurity incident report is a critical step in incident response. How to write a cybersecurity incident report. This template has been developed by the national cybersecurity authority (nca) as an illustrative example that can be used by organizations as a reference and guide. They enable you to compile comprehensive. Browse upguard's library of free templates for all major cybersecurity standards, frameworks and regulations. The global cybersecurity outlook 2025 highlights key trends shaping economies and societies in 2025, along with insights into emerging threats and solutions. In this article, you’ll find the most effective cybersecurity risk assessment templates for project managers, security analysts, security incident responders, intrusion detection. Using a. Get a free and fillable cybersecurity incident report template. How to write a cybersecurity incident report. The global cybersecurity outlook 2025 highlights key trends shaping economies and societies in 2025, along with insights into emerging threats and solutions. Neglecting strong, thoroughly tested, and dependable security measures can leave you vulnerable to malicious attacks. If you'd like to learn more about. Using a structured cyber incident report template, firms efficiently communicate details related to a security breach or incident. Some 72% of respondents report an increase in organizational cyber risks, with ransomware remaining a top concern. A cyber incident report template captures. Download and edit a professional cyber security report example. Simplify documentation of breaches, viruses, and other it security events. If you'd like to learn more about our. Security safeguards to ensure cyber resilience. The global cybersecurity outlook 2025 highlights key trends shaping economies and societies in 2025, along with insights into emerging threats and solutions. Safeguard your business with a robust security report. How to write a cybersecurity incident report. These templates offer a streamlined, professional solution to the complex challenges of cyber security reporting. Free security audit report template. Neglecting strong, thoroughly tested, and dependable security measures can leave you vulnerable to malicious attacks. Get insights and templates to enhance your cybersecurity documentation The global cybersecurity outlook 2025 highlights key trends shaping economies and societies in 2025, along with. How is this report done? How to write a cybersecurity incident report. Our free printable templates help you log risks, incidents, controls and recommendations. The global cybersecurity outlook 2025 highlights key trends shaping economies and societies in 2025, along with insights into emerging threats and solutions. Get insights and templates to enhance your cybersecurity documentation Writing an effective cybersecurity incident report is a critical step in incident response. The cyber risk assessment powerpoint template is a visually structured tool designed to help businesses, it teams, and security professionals analyze and present cyber threats. These templates offer a streamlined, professional solution to the complex challenges of cyber security reporting. A cybersecurity report contains vital details regarding cybersecurity issues, vulnerabilities in the digital environment, safety controls weaknesses, and security program effectiveness. Here we present to you our top 5 security report templates to explain the need and importance of a security report. Simplify documentation of breaches, viruses, and other it security events. Create the perfect defence against cyber crimes with our comprehensive security report templates. Security safeguards to ensure cyber resilience. In this article, you’ll find the most effective cybersecurity risk assessment templates for project managers, security analysts, security incident responders, intrusion detection. Get insights and templates to enhance your cybersecurity documentation The global cybersecurity outlook 2025 highlights key trends shaping economies and societies in 2025, along with insights into emerging threats and solutions. This template has been developed by the national cybersecurity authority (nca) as an illustrative example that can be used by organizations as a reference and guide. Download in xls & pdf formats. How is this report done? Cyber security under the reporting standards. Once the dma is completed, you can move on to the data collection phase.Cyber Security Report Template Collection
Cyber Security Board Report Template
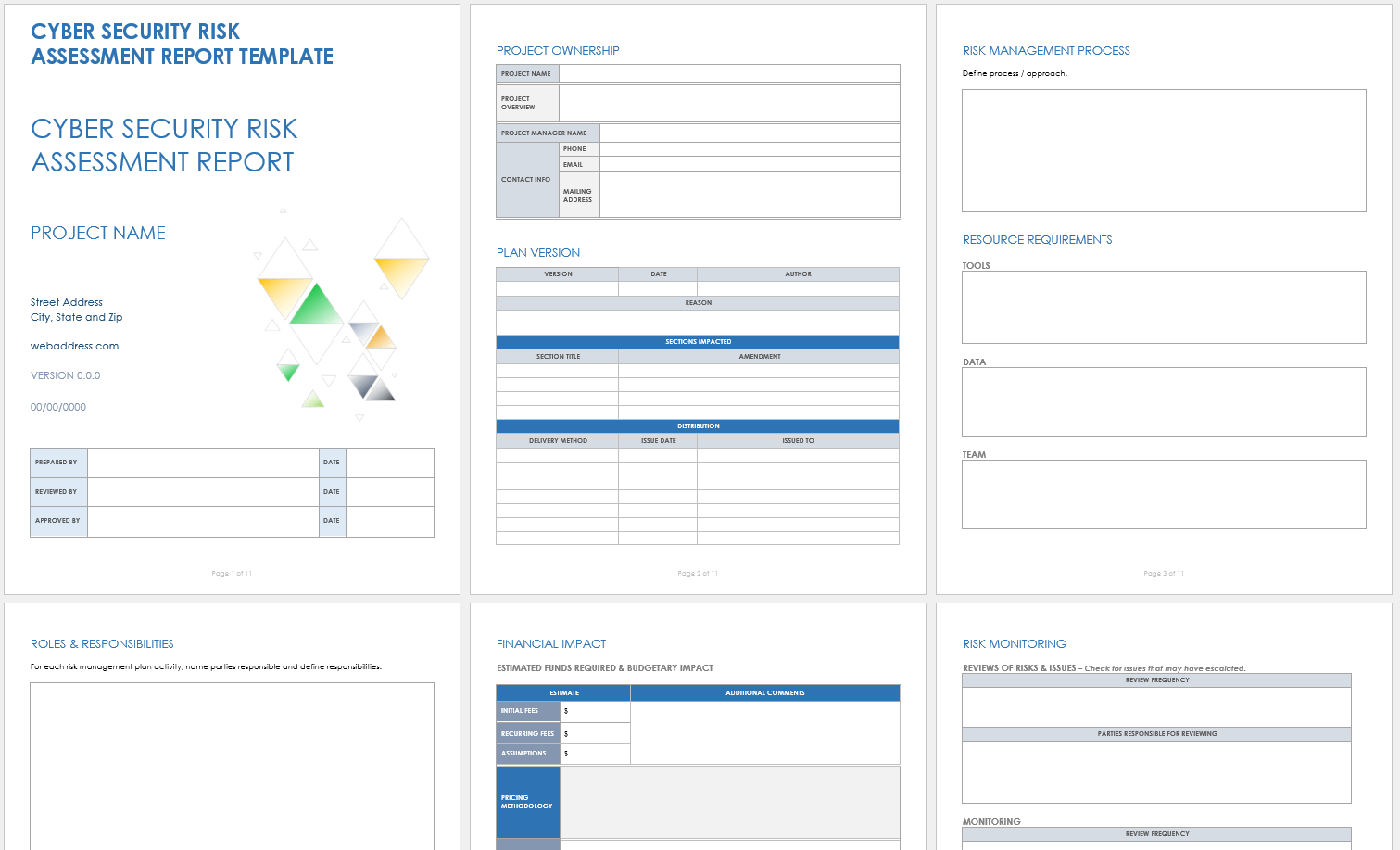
Free Cybersecurity Risk Assessment Templates Smartsheet
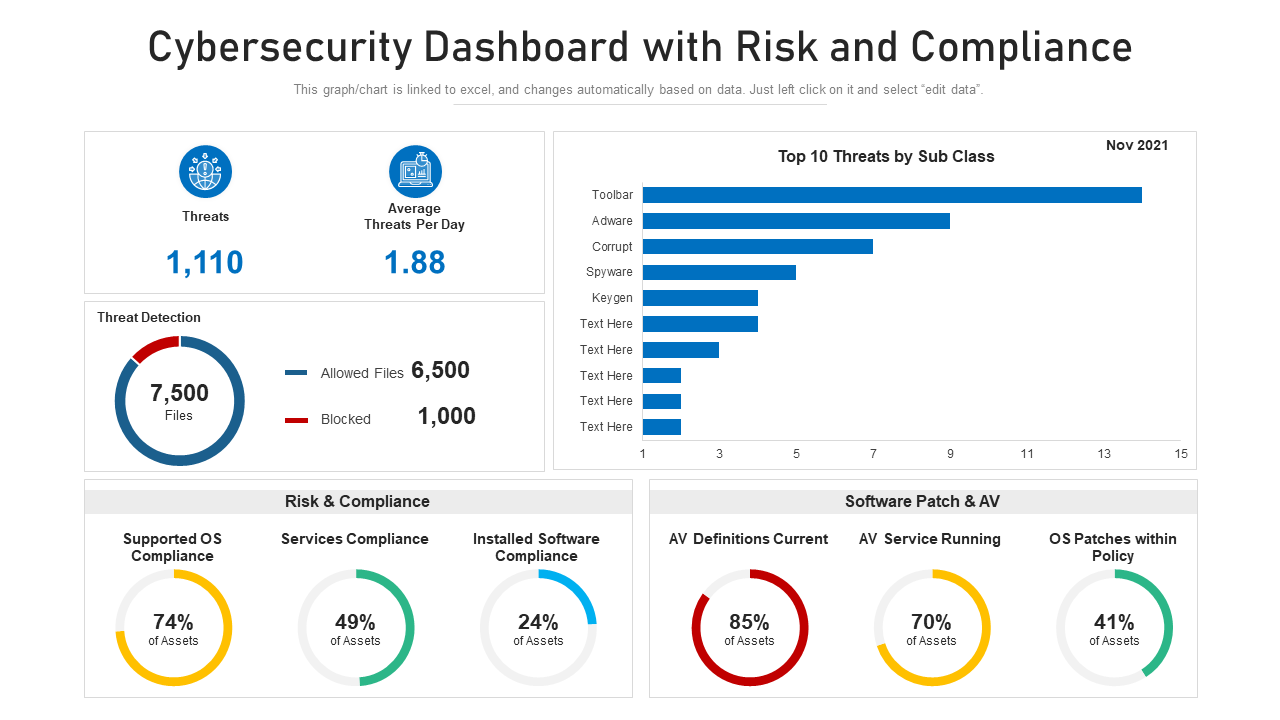
Top 10 Cybersecurity Dashboard Templates With Samples and Examples
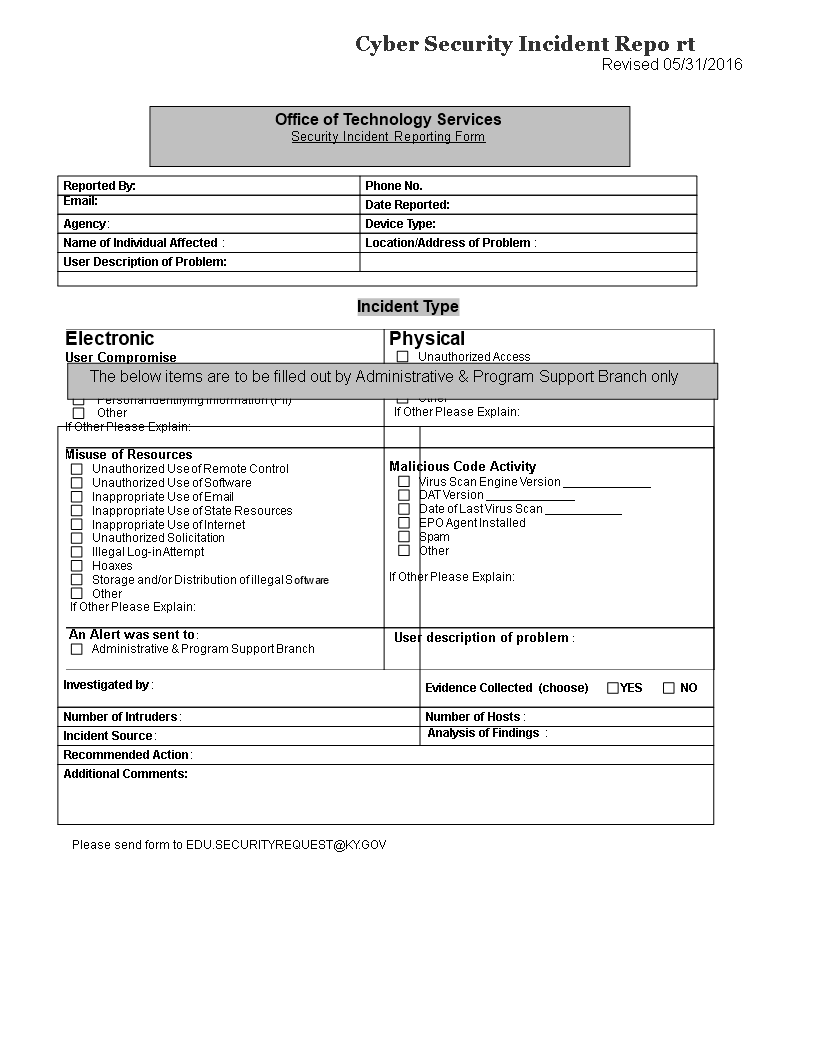
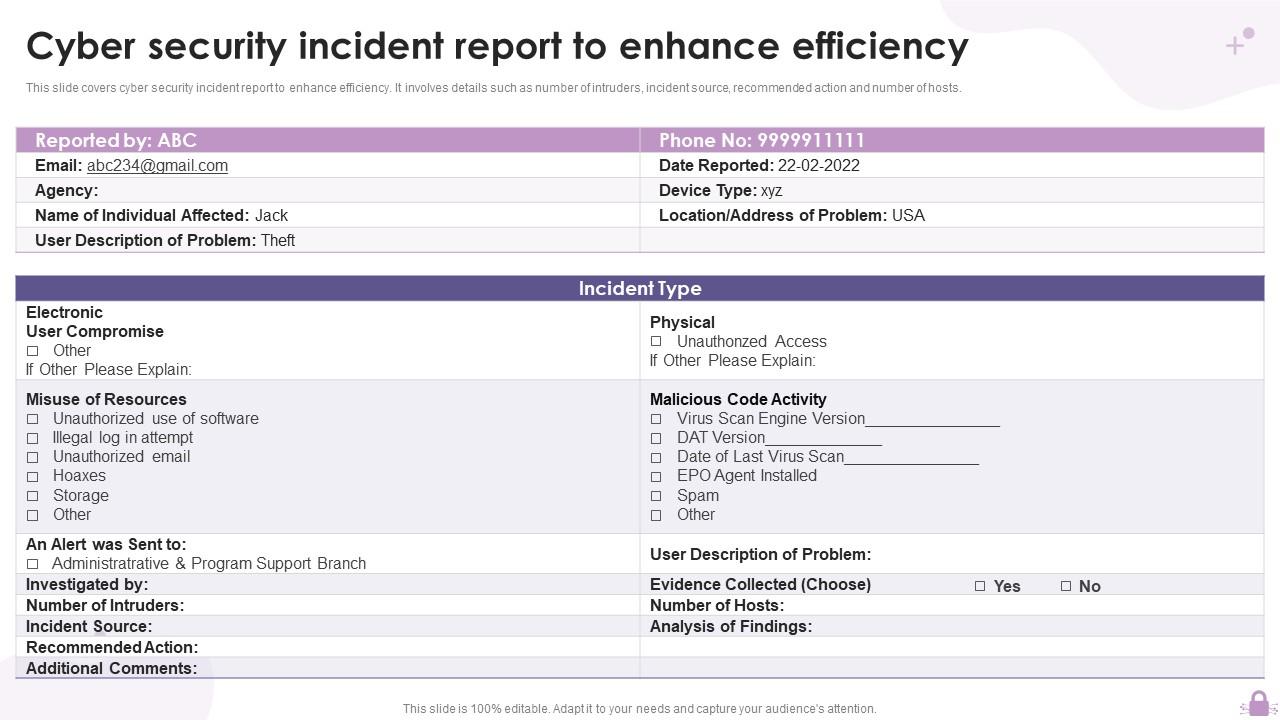
Free Cybersecurity (IT) Incident Report Template PDF Word eForms
Cybersecurity Report Template
Cyber Security Incident Report template Templates at
Cyber Security Report Template Word
Cyber Security Report Template
Top 5 Cyber Security Report Templates with Samples and Examples
Six Months After The Sec’s Cybersecurity Incident Disclosure Rule (Sec Rule) Came Into Force, An April 2024 Gt Alert Summarized Disclosure Trends.
Browse Upguard's Library Of Free Templates For All Major Cybersecurity Standards, Frameworks And Regulations.
Free Security Audit Report Template.
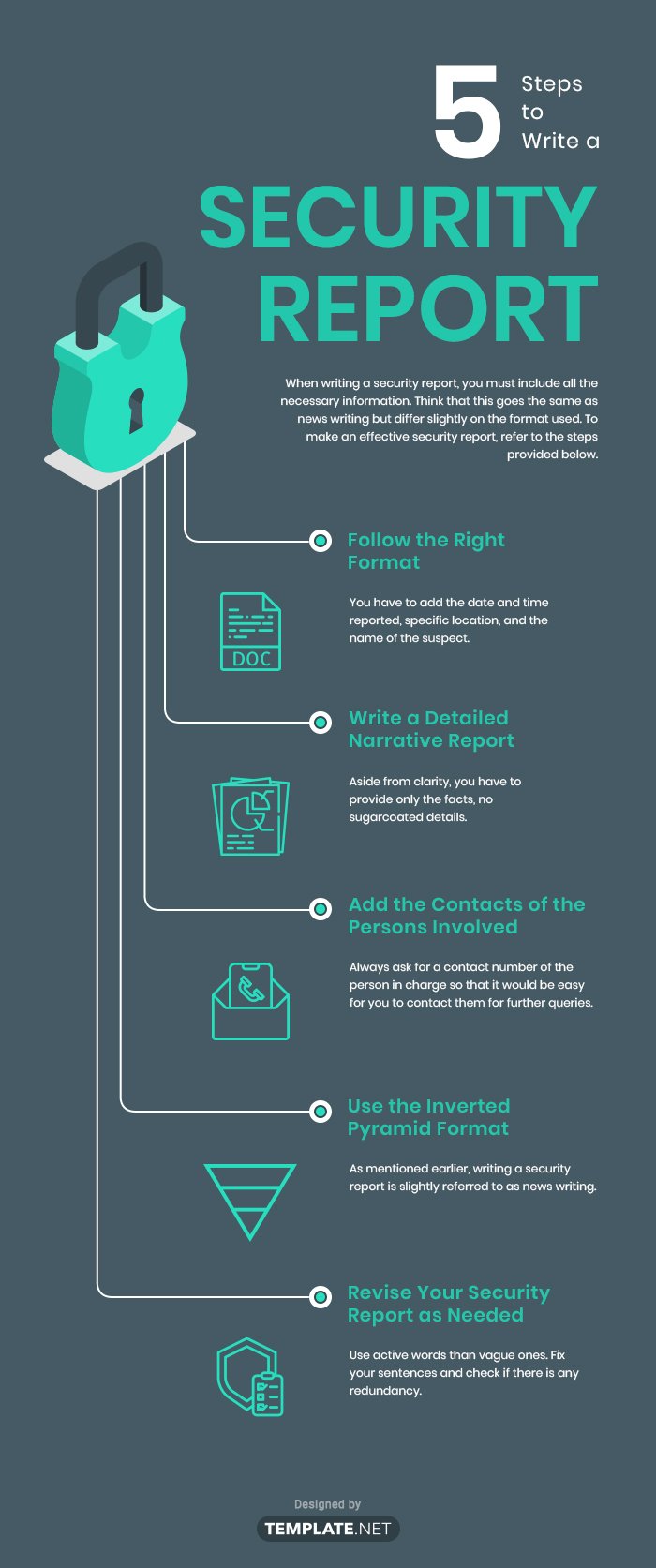
A Security Report Is A Detailed Document That Records Security Incidents, Risks, And Threats, Providing Analysis And Recommendations For Prevention.
Related Post: