Nist Incident Response Playbook Template
Nist Incident Response Playbook Template - The nist’s cybersecurity incident handling guide seeks to empower businesses to bolster their security posture and incident response capabilities through adequate preparation, cybersecurity training, planning and optimal resource allocation. Because performing incident response effectively is a complex undertaking, establishing a successful incident response capability requires substantial planning and. 2, computer security incident handling guide. This repository contains all the incident response playbooks and workflows of company's soc. The guidelines can be followed independently of particular hardware platforms, operating systems, protocols, or. Incident response programs are critical and this incident response scenario playbook will strengthen the skills you and your organization need to be prepared. These playbooks provide fceb agencies with a standard set of procedures to identify, coordinate, remediate, recover, and track successful mitigations from incidents and vulnerabilities affecting fceb systems, data, and networks. Created by the experts behind the uk's ncsc assured training in building and optimising incident response playbooks, this template contains all the key elements of a good ir playbook. This repository contains all the incident response playbooks and workflows of company's soc. Computer security incident response has become an important component of information technology (it) programs. Incident response programs are critical and this incident response scenario playbook will strengthen the skills you and your organization need to be prepared. The guidelines can be followed independently of particular hardware platforms, operating systems, protocols, or. This repository contains all the incident response playbooks and workflows of company's soc. Created by the experts behind the uk's ncsc assured training in building and optimising incident response playbooks, this template contains all the key elements of a good ir playbook. Because performing incident response effectively is a complex undertaking, establishing a successful incident response capability requires substantial planning and. These playbooks provide fceb agencies with a standard set of procedures to identify, coordinate, remediate, recover, and track successful mitigations from incidents and vulnerabilities affecting fceb systems, data, and networks. This repository contains all the incident response playbooks and workflows of company's soc. Computer security incident response has become an important component of information technology (it) programs. 2, computer security incident handling guide. The nist’s cybersecurity incident handling guide seeks to empower businesses to bolster their security posture and incident response capabilities through adequate preparation, cybersecurity training, planning and optimal resource allocation. The guidelines can be followed independently of particular hardware platforms, operating systems, protocols, or. This repository contains all the incident response playbooks and workflows of company's soc. This repository contains all the incident response playbooks and workflows of company's soc. The nist’s cybersecurity incident handling guide seeks to empower businesses to bolster their security posture and incident response capabilities through. 2, computer security incident handling guide. The nist’s cybersecurity incident handling guide seeks to empower businesses to bolster their security posture and incident response capabilities through adequate preparation, cybersecurity training, planning and optimal resource allocation. The guidelines can be followed independently of particular hardware platforms, operating systems, protocols, or. This repository contains all the incident response playbooks and workflows of. 2, computer security incident handling guide. Because performing incident response effectively is a complex undertaking, establishing a successful incident response capability requires substantial planning and. Created by the experts behind the uk's ncsc assured training in building and optimising incident response playbooks, this template contains all the key elements of a good ir playbook. The guidelines can be followed independently. These playbooks provide fceb agencies with a standard set of procedures to identify, coordinate, remediate, recover, and track successful mitigations from incidents and vulnerabilities affecting fceb systems, data, and networks. This repository contains all the incident response playbooks and workflows of company's soc. This repository contains all the incident response playbooks and workflows of company's soc. Computer security incident response. The guidelines can be followed independently of particular hardware platforms, operating systems, protocols, or. Incident response programs are critical and this incident response scenario playbook will strengthen the skills you and your organization need to be prepared. Created by the experts behind the uk's ncsc assured training in building and optimising incident response playbooks, this template contains all the key. Created by the experts behind the uk's ncsc assured training in building and optimising incident response playbooks, this template contains all the key elements of a good ir playbook. This repository contains all the incident response playbooks and workflows of company's soc. Computer security incident response has become an important component of information technology (it) programs. 2, computer security incident. The guidelines can be followed independently of particular hardware platforms, operating systems, protocols, or. Created by the experts behind the uk's ncsc assured training in building and optimising incident response playbooks, this template contains all the key elements of a good ir playbook. Computer security incident response has become an important component of information technology (it) programs. Because performing incident. Incident response programs are critical and this incident response scenario playbook will strengthen the skills you and your organization need to be prepared. 2, computer security incident handling guide. Because performing incident response effectively is a complex undertaking, establishing a successful incident response capability requires substantial planning and. The nist’s cybersecurity incident handling guide seeks to empower businesses to bolster. The guidelines can be followed independently of particular hardware platforms, operating systems, protocols, or. Because performing incident response effectively is a complex undertaking, establishing a successful incident response capability requires substantial planning and. Incident response programs are critical and this incident response scenario playbook will strengthen the skills you and your organization need to be prepared. 2, computer security incident. Created by the experts behind the uk's ncsc assured training in building and optimising incident response playbooks, this template contains all the key elements of a good ir playbook. 2, computer security incident handling guide. Incident response programs are critical and this incident response scenario playbook will strengthen the skills you and your organization need to be prepared. This repository. This repository contains all the incident response playbooks and workflows of company's soc. Computer security incident response has become an important component of information technology (it) programs. Because performing incident response effectively is a complex undertaking, establishing a successful incident response capability requires substantial planning and. Created by the experts behind the uk's ncsc assured training in building and optimising incident response playbooks, this template contains all the key elements of a good ir playbook. This repository contains all the incident response playbooks and workflows of company's soc. Incident response programs are critical and this incident response scenario playbook will strengthen the skills you and your organization need to be prepared. These playbooks provide fceb agencies with a standard set of procedures to identify, coordinate, remediate, recover, and track successful mitigations from incidents and vulnerabilities affecting fceb systems, data, and networks. The guidelines can be followed independently of particular hardware platforms, operating systems, protocols, or.Nist Incident Response Playbook Template
Top 13 Templates to Build an Incident Response Playbook The SlideTeam
Incident Response Playbook Template
NIST Incident Response Playbook Template
Nist Incident Response Playbook Template
Nist Incident Response Playbook Template
Playbooks and Runbooks for Incident Response DEVSECOPS ON AWS USING
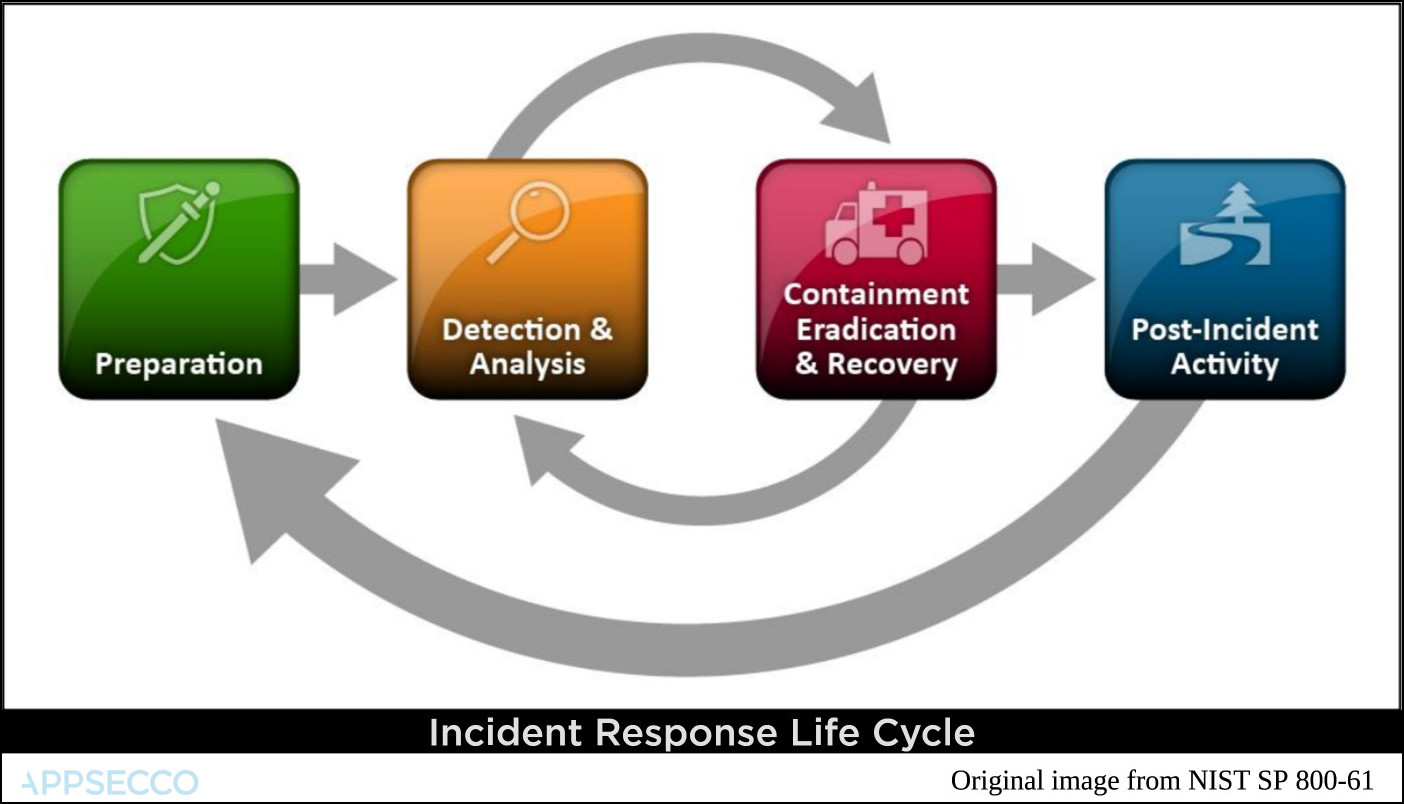
NIST for Computer Security Incident Handling Clear
NIST Incident Response Your GoTo Guide to Handling Cybersecurity
Developing an incident response playbook Securelist
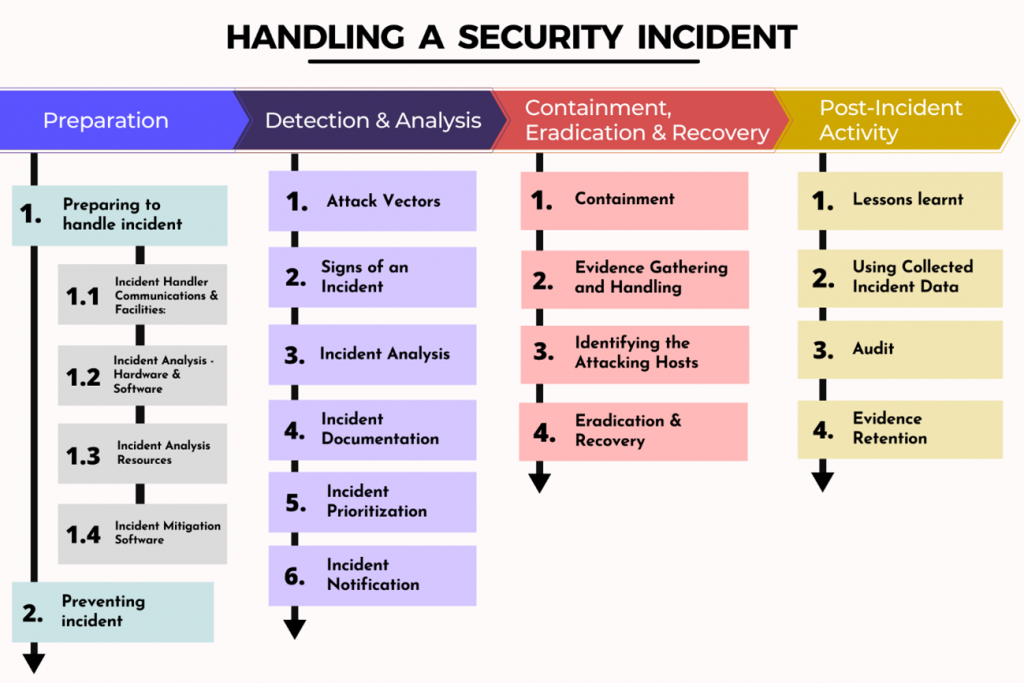
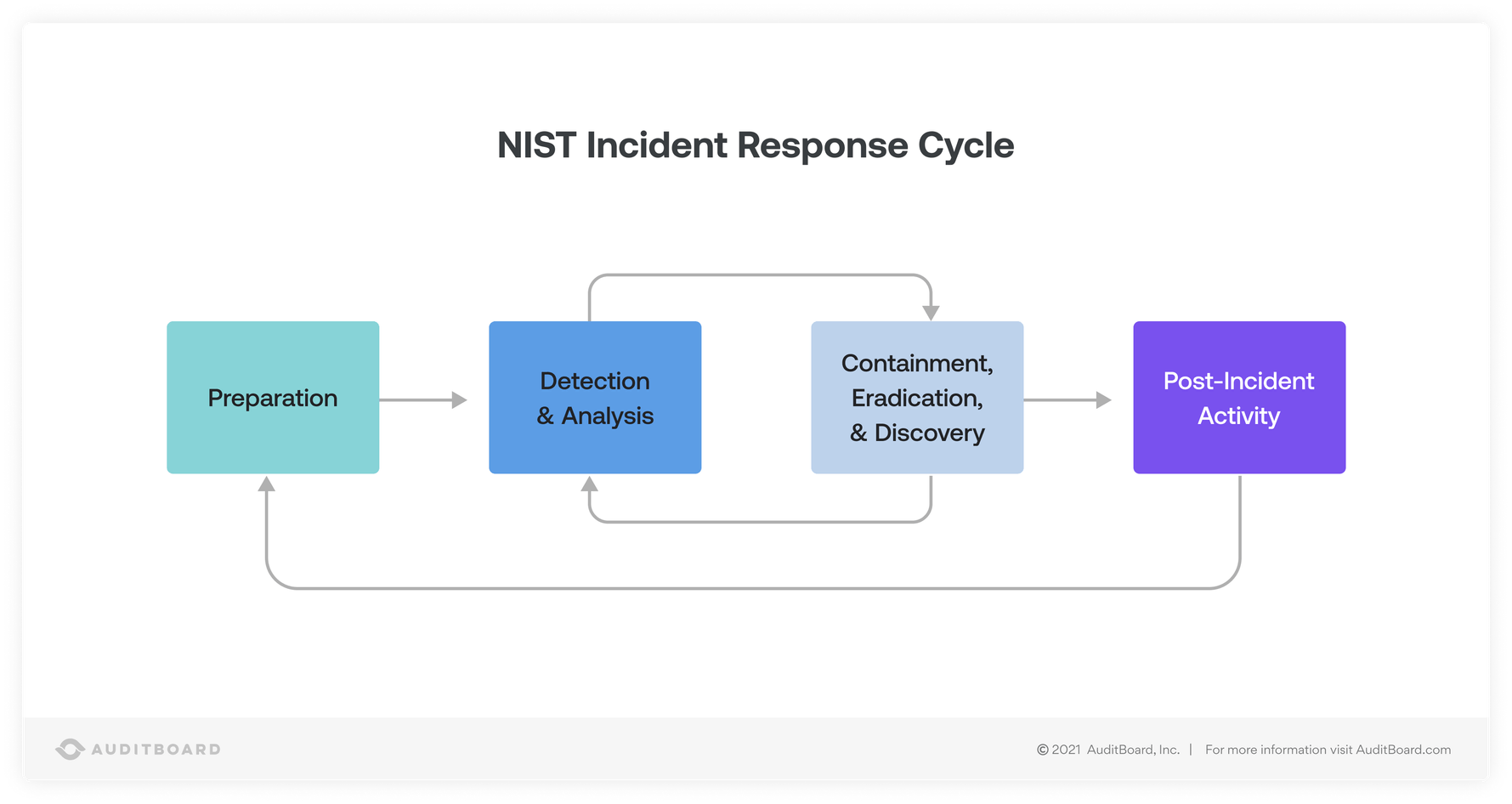
2, Computer Security Incident Handling Guide.
The Nist’s Cybersecurity Incident Handling Guide Seeks To Empower Businesses To Bolster Their Security Posture And Incident Response Capabilities Through Adequate Preparation, Cybersecurity Training, Planning And Optimal Resource Allocation.
Related Post: