Vulnerability Remediation Plan Template
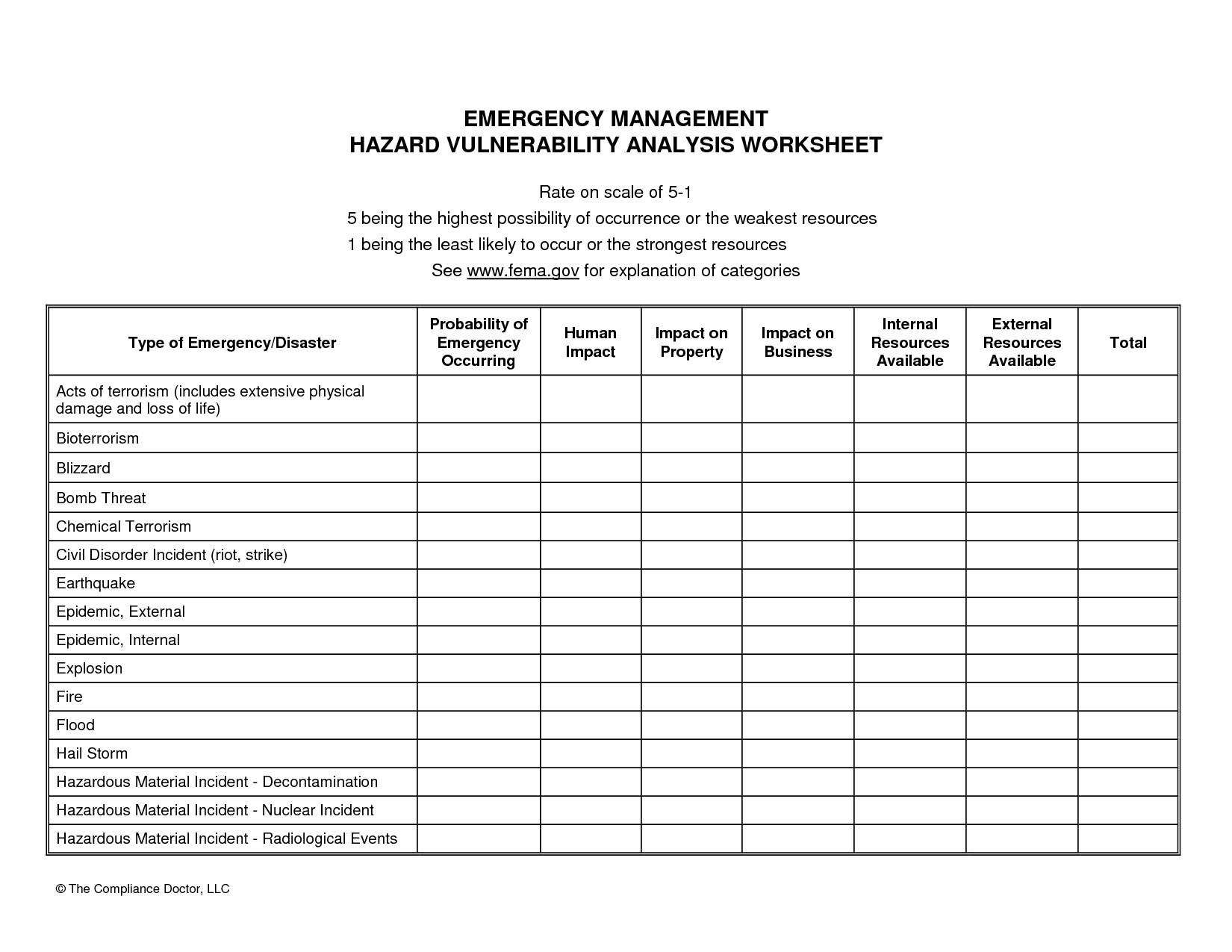
Vulnerability Remediation Plan Template - An action plan for remediation, fixing the identified gaps and patching targeted systems/applications, must be developed. A good example of a vulnerability in a business setting is when there is a weakness in a firewall that lets hackers get into a computer network. Using a template for your plan helps you spend more time on what. System updates, patches, scanning, endpoint protection, and more all help an organization understand and mitigate vulnerabilities that may exist in within its it environment. Each document is designed to serve as a comprehensive guide for organizations to formulate and implement their vulnerability management policies. There are 8 best practices when planning your vulnerability remediation including prioritization of vulnerabilities, setting timelines, defining a slo, developing a remediation policy, automating. They cover a range of. How to create a security remediation plan? Vulnerability patch management is a continuous process of identifying, prioritizing, remediating, and reporting on security vulnerabilities in systems. The steps include the following: How to create a security remediation plan? A plan of action to address identified vulnerabilities. This vulnerability management plan template provides a structure and guidance to help create a comprehensive plan that identifies and mitigates security risks, threats, and other potential. A good example of a vulnerability in a business setting is when there is a weakness in a firewall that lets hackers get into a computer network. Vulnerability patch management is a continuous process of identifying, prioritizing, remediating, and reporting on security vulnerabilities in systems. The steps include the following: There are 8 best practices when planning your vulnerability remediation including prioritization of vulnerabilities, setting timelines, defining a slo, developing a remediation policy, automating. You can save time by downloading one of our free printable remediation plan templates in pdf, word, and excel formats. Vulnerability management is critical in today’s environment due to the increasing complexity of it systems and the evolving threat landscape. Using a template for your plan helps you spend more time on what. Vulnerability patch management is a continuous process of identifying, prioritizing, remediating, and reporting on security vulnerabilities in systems. A risk remediation plan is a roadmap that identifies and addresses possible vulnerabilities within an organisation’s working structure and infrastructure. Vulnerability remediation is the process of addressing system security weaknesses. In this article, we will lay out a template for a vulnerability. The highest priority items are determined. A plan of action to address identified vulnerabilities. A good example of a vulnerability in a business setting is when there is a weakness in a firewall that lets hackers get into a computer network. They cover a range of. There are 8 best practices when planning your vulnerability remediation including prioritization of vulnerabilities,. They cover a range of. The steps include the following: Steps taken to reduce or eliminate a vulnerability. Each document is designed to serve as a comprehensive guide for organizations to formulate and implement their vulnerability management policies. An action plan for remediation, fixing the identified gaps and patching targeted systems/applications, must be developed. The plan must include vulnerabilities details,. A plan of action to address identified vulnerabilities. A good example of a vulnerability in a business setting is when there is a weakness in a firewall that lets hackers get into a computer network. Vulnerability management is critical in today’s environment due to the increasing complexity of it systems and the evolving threat. A plan of action to address identified vulnerabilities. Vulnerability management is critical in today’s environment due to the increasing complexity of it systems and the evolving threat landscape. Vulnerability remediation is the process of addressing system security weaknesses. An action plan for remediation, fixing the identified gaps and patching targeted systems/applications, must be developed. The steps include the following: A risk remediation plan is a roadmap that identifies and addresses possible vulnerabilities within an organisation’s working structure and infrastructure. Using a template for your plan helps you spend more time on what. Vulnerability patch management is a continuous process of identifying, prioritizing, remediating, and reporting on security vulnerabilities in systems. In this article, we will lay out a template. A good example of a vulnerability in a business setting is when there is a weakness in a firewall that lets hackers get into a computer network. Steps taken to reduce or eliminate a vulnerability. A risk remediation plan is a roadmap that identifies and addresses possible vulnerabilities within an organisation’s working structure and infrastructure. There are 8 best practices. A good example of a vulnerability in a business setting is when there is a weakness in a firewall that lets hackers get into a computer network. Vulnerability management is critical in today’s environment due to the increasing complexity of it systems and the evolving threat landscape. Vulnerability patch management is a continuous process of identifying, prioritizing, remediating, and reporting. A risk remediation plan is a roadmap that identifies and addresses possible vulnerabilities within an organisation’s working structure and infrastructure. A good example of a vulnerability in a business setting is when there is a weakness in a firewall that lets hackers get into a computer network. There are 8 best practices when planning your vulnerability remediation including prioritization of. A plan of action to address identified vulnerabilities. The steps include the following: There are 8 best practices when planning your vulnerability remediation including prioritization of vulnerabilities, setting timelines, defining a slo, developing a remediation policy, automating. Vulnerability patch management is a continuous process of identifying, prioritizing, remediating, and reporting on security vulnerabilities in systems. System updates, patches, scanning, endpoint. An action plan for remediation, fixing the identified gaps and patching targeted systems/applications, must be developed. Steps taken to reduce or eliminate a vulnerability. There are 8 best practices when planning your vulnerability remediation including prioritization of vulnerabilities, setting timelines, defining a slo, developing a remediation policy, automating. Vulnerability patch management is a continuous process of identifying, prioritizing, remediating, and reporting on security vulnerabilities in systems. Vulnerability management is critical in today’s environment due to the increasing complexity of it systems and the evolving threat landscape. Each document is designed to serve as a comprehensive guide for organizations to formulate and implement their vulnerability management policies. Vulnerability remediation is the process of addressing system security weaknesses. How to create a security remediation plan? The steps include the following: You can save time by downloading one of our free printable remediation plan templates in pdf, word, and excel formats. They cover a range of. System updates, patches, scanning, endpoint protection, and more all help an organization understand and mitigate vulnerabilities that may exist in within its it environment. A risk remediation plan is a roadmap that identifies and addresses possible vulnerabilities within an organisation’s working structure and infrastructure. The plan must include vulnerabilities details,. This vulnerability management plan template provides a structure and guidance to help create a comprehensive plan that identifies and mitigates security risks, threats, and other potential. A good example of a vulnerability in a business setting is when there is a weakness in a firewall that lets hackers get into a computer network.ICVulnerabilityRemediationPlanTemplate_Google.xltx Google Sheets
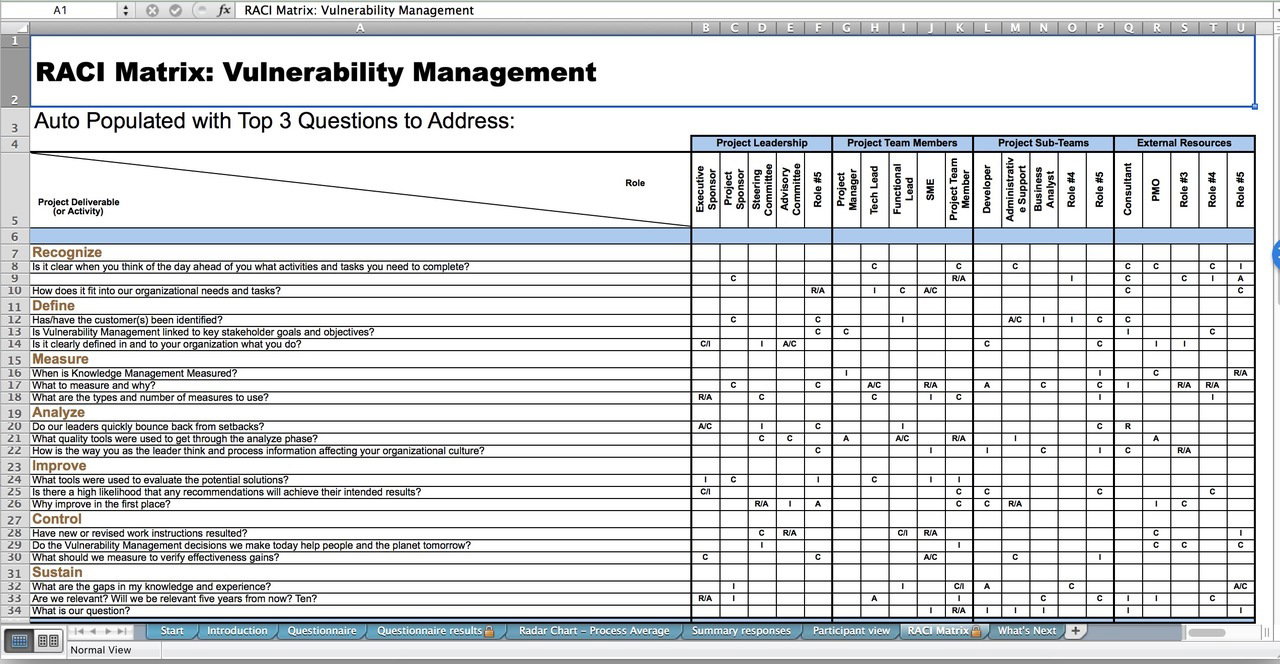
Vulnerability Management Policy Template
Vulnerability Management Process Template
Vulnerability Remediation Plan Template at vanboblog Blog
Vulnerability Management Plan Template
Patch And Vulnerability Management Plan Template
Vulnerability Remediation Plan Template at vanboblog Blog
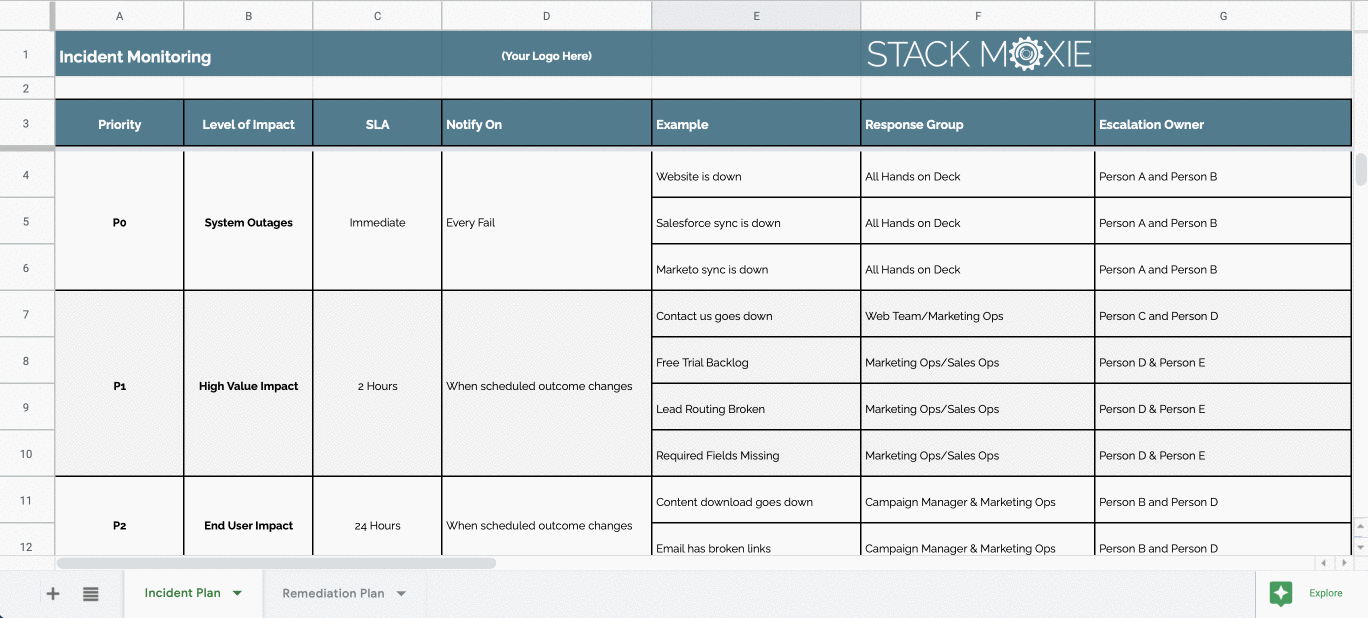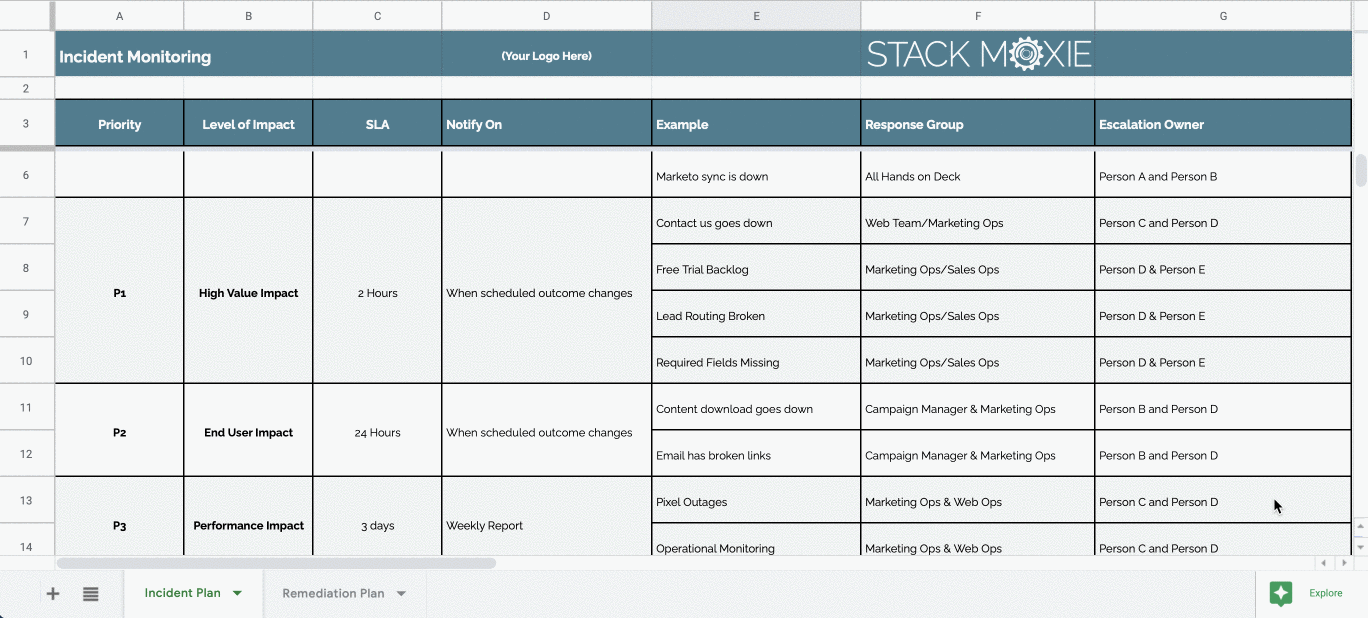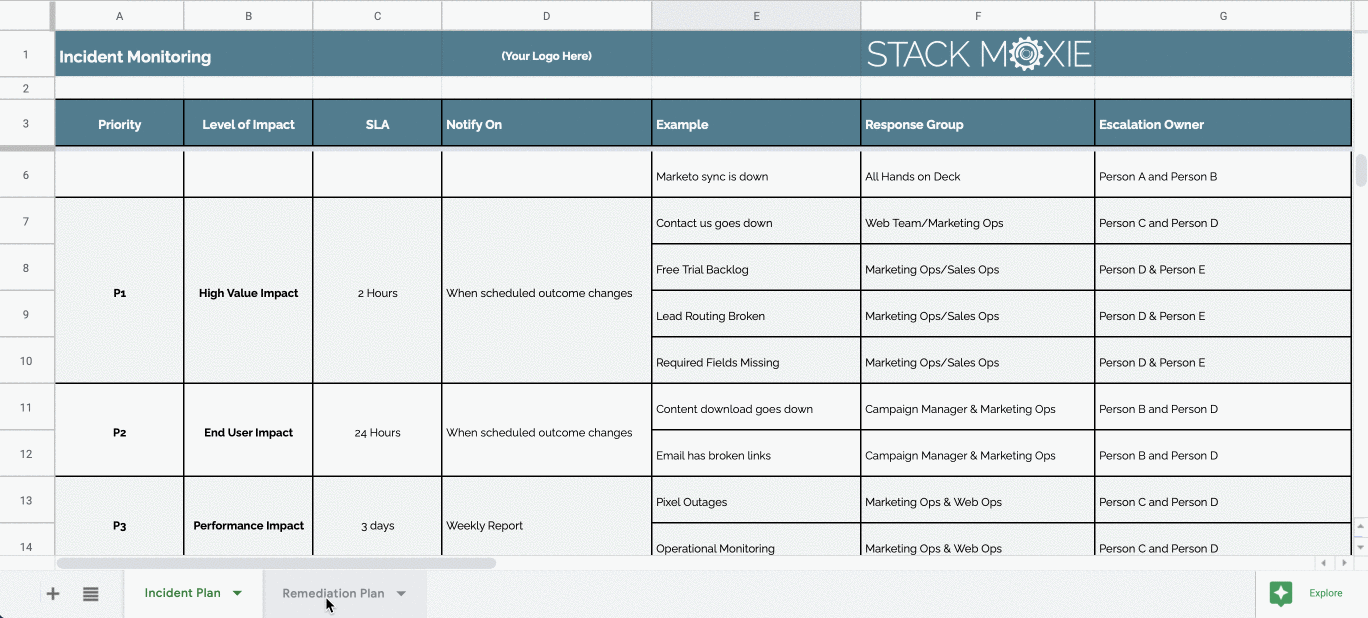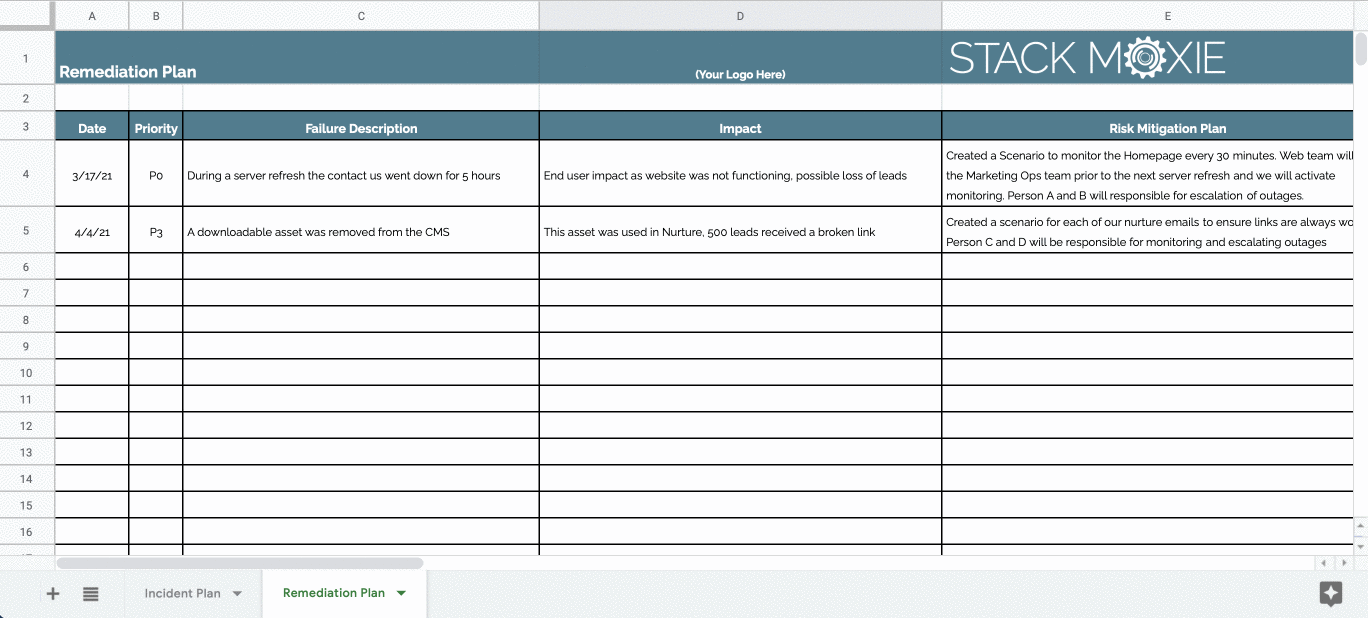
Incident & Remediation Plan Template for managing critical errors and
Vulnerability Remediation Plan Template at vanboblog Blog
Vulnerability Remediation Plan Template
The Highest Priority Items Are Determined.
A Plan Of Action To Address Identified Vulnerabilities.
In This Article, We Will Lay Out A Template For A Vulnerability Remediation Plan Your Organization Can Follow That Will Streamline Processes, Lower Costs, And Immediately Mitigate Risk.
Using A Template For Your Plan Helps You Spend More Time On What.
Related Post: